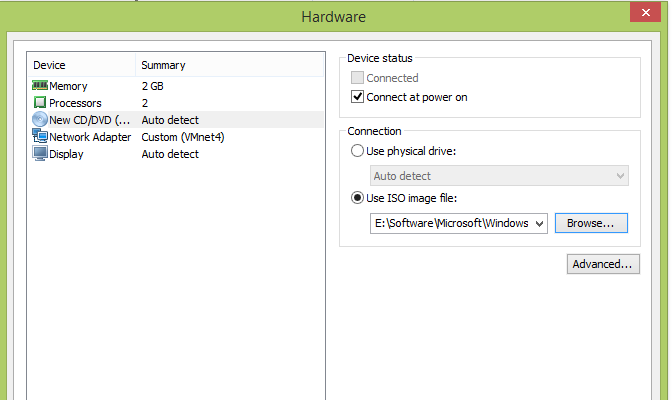
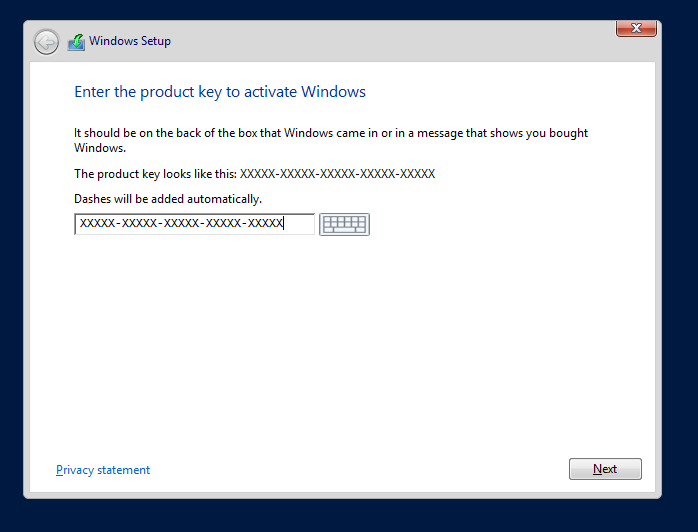
We will need LDAPS later on for the two factor authentication, using openOTP
The suggested solution of the OpenOTP is not best practice, they suggest setting up a CA on the domain controller.
This Microsoft article is providing the necessary information’s
http://social.technet.microsoft.com/wiki/contents/articles/2980.ldap-over-ssl-ldaps-certificate.aspx
Template – Enhanced Key Usage – Server Authentication (1.3.6.1.5.5.7.3.1) is important
Place the certificate
how to add the certificate to the NTDS service’s Personal certificate store
http://technet.microsoft.com/en-us/library/dd941846(WS.10).aspx
for troubleshooting
http://support.microsoft.com/kb/938703
Requesting and installing a certificate
Create the CSR
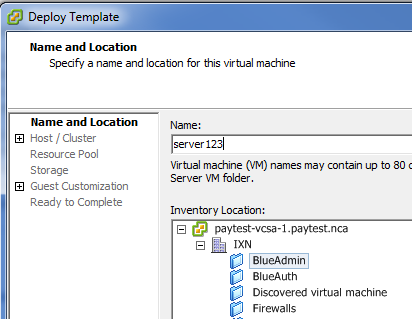
Logon
Create a CSR on the core server
certreq -new c:\temp\cert.inf c:\temp\certrequest.req
the cert.inf file:
[NewRequest]
Subject=”C=CH,S=ZH,L=Zurich,O=Company,OU=IT,CN=server.domain.local”
PrivateKeyArchive=FALSE
Exportable=FALSE
UserProtected=FALSE
MachineKeySet=TRUE
ProviderName=”Microsoft RSA SChannel Cryptographic Provider”
ProviderType=12
UseExistingKeySet=FALSE
RequestType=PKCS10
HashAlgorithm=sha256
KeyLength=4096
KeyUsage = 0xF0 ; Digital Signature, Key Encipherment, Nonrepudiation, Data Encipherment
KeySpec=1
[EnhancedKeyUsageExtension]
OID=1.3.6.1.5.5.7.3.1 ; Server Authentication
Sign the Certificate at the CA
Install the certificate
certreq -accept c:\temp\SignedCertificate.cer
Install the Root certificate
Do not forget to install the root certificate into the machine “trusted store”
Certutil –addstore –f “TrustedPublisher” c:\temp\root.cer
Verification
After a certificate is installed, follow these steps to verify that LDAPS is enabled:
- Start the Active Directory Administration Tool (Ldp.exe)
- On the Connection menu, click Connect.
- Type the name of the LDAP server (e.g. domain controller or AD LDS/ADAM server) to which you want to connect.
- Type 636 as the port number.
- Click OK.
Debug in case of problems
Certutil –VerifyStore MY
result:
MY “Personal”
================ Certificate 0 ================
Serial Number: 75000000088db1a509904b6eff000000000008
Issuer: CN=XCA01-CA
NotBefore: 24.06.2015 09:03
NotAfter: 24.06.2016 09:13
Subject: CN=xdc01.xjbk.local
Non-root Certificate
Cert Hash(sha1): 1e 8b df 3f 67 1c 18 fe a9 7d 2b 32 0d d2 1a a3 9f 17 8c fd
Key Container = 87698826a058b37df04eac8a815a9b98_837e2fc9-5182-4419-9660-e414d
e50a998
Simple container name: CertReq-0ecbfed1-329c-4ac6-a5ec-246aa7b87939
Provider = Microsoft RSA SChannel Cryptographic Provider
Private key is NOT exportable
Encryption test passed
Revocation check skipped — server offline
Certificate is valid
CertUtil: -verifystore command completed successfully.
Technical Information:
How to enable LDAP over SSL with external CA
https://support.microsoft.com/de-ch/kb/321051/en-us
https://technet.microsoft.com/en-us/library/cc736326.aspx